AppRecs review analysis
AppRecs rating 3.1. Trustworthiness 85 out of 100. Review manipulation risk 22 out of 100. Based on a review sample analyzed.
★★★☆☆
3.1
AppRecs Rating
Ratings breakdown
5 star
46%
4 star
7%
3 star
7%
2 star
11%
1 star
29%
What to know
✓
Low review manipulation risk
22% review manipulation risk
✓
Credible reviews
85% trustworthiness score from analyzed reviews
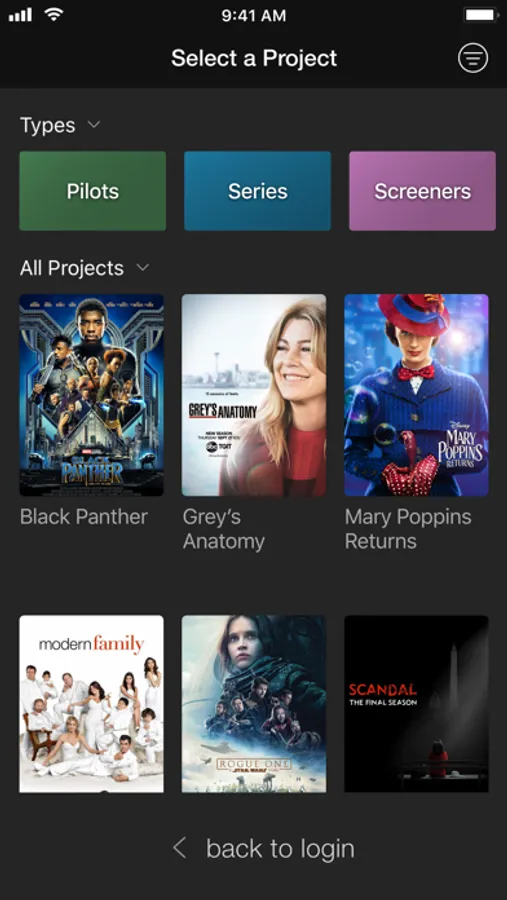
About PIX System
PIX for iOS provides secure access to your projects, whether connected in the office or offline on an airplane. Search, share, make notes and approve items with one touch.
Capabilities:
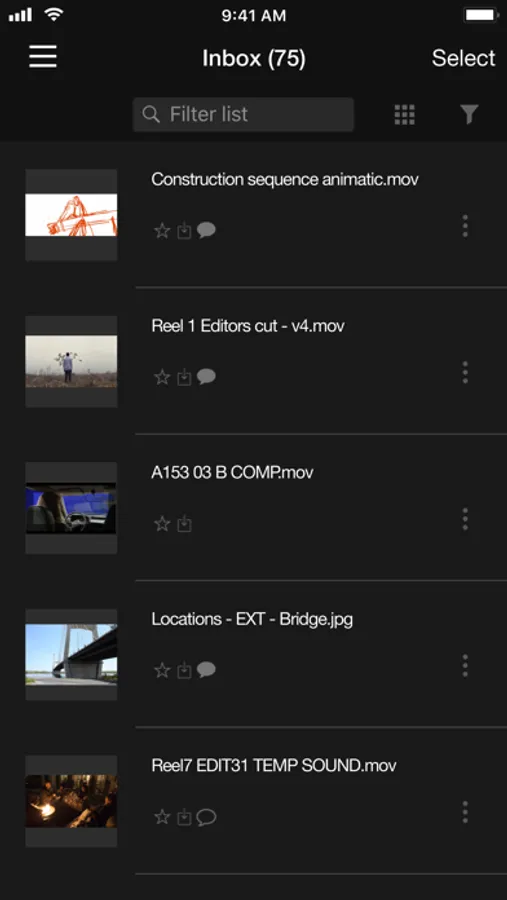
Intuitive Review Tools
- Familiar inbox for fast navigation to desired content, and playlists for sharing and managing files
- Keyword search for clips, playlists, tags or notes
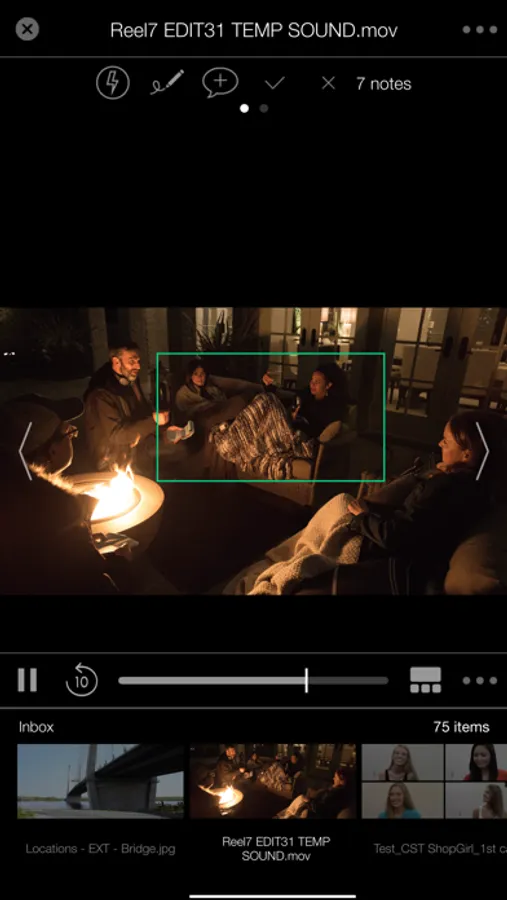
- Frame and page-specific markup
- One touch approvals
- Customizable quick notes
Multiple Viewing Options
- Mirror or AirPlay to a second device, including Apple TV
- Offline viewing with DRM
Integrated Production Workflow
- Metadata tracking from production through final release to facilitate client workflows
- Progress across devices synchronized for resume playback and notes and approvals
- Integrations leveraging industry tools, as well as custom integrations
Industry-Leading Security
- Visual and forensic watermarking, customizable by group
- End-to-end encryption
- Two-factor authentication (2FA) and other user access controls
- Threat monitoring and 24/7 user activity logging
Capabilities:
Intuitive Review Tools
- Familiar inbox for fast navigation to desired content, and playlists for sharing and managing files
- Keyword search for clips, playlists, tags or notes
- Frame and page-specific markup
- One touch approvals
- Customizable quick notes
Multiple Viewing Options
- Mirror or AirPlay to a second device, including Apple TV
- Offline viewing with DRM
Integrated Production Workflow
- Metadata tracking from production through final release to facilitate client workflows
- Progress across devices synchronized for resume playback and notes and approvals
- Integrations leveraging industry tools, as well as custom integrations
Industry-Leading Security
- Visual and forensic watermarking, customizable by group
- End-to-end encryption
- Two-factor authentication (2FA) and other user access controls
- Threat monitoring and 24/7 user activity logging